If you or your department are considering new applications, software, or services ITS can help. The ITS team is involved with hundreds of applications at all stages of the application lifecycle and can help you select and purchase the right information technology tool(s) for you, the department, and the University.
To request Application Selection & Procurement services, just submit a work order ticket. (Use the category Consulting Services -> New Applications). Your request will be routed to the appropriate analyst who will contact you, help gather information, and complete the forms necessary for getting purchase requisitions and contract approvals.
ATSU Policy 55-102: Hardware/Software Procurement Procedure requires purchases of all computer hardware, software, and services to be coordinated with Information Technology Services (ITS). This coordination helps ensure systems, services, and related technologies are evaluated from a variety of perspectives including.
- Inventory of all systems/services used by ATSU
- Data Classification and data governance
- Cybersecurity
- Licensing and ongoing operating costs
- Integration with existing systems and the ATSU network
- Code ownership
- Contract terms
- Vendor management, ongoing maintenance, and administration
- Measuring system usage and value
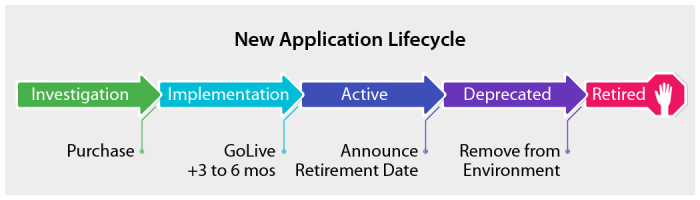
Below is a checklist to help guide you through the 2 steps of the procurement process.
STEP 1: Evaluating the Marketplace & Vendor Selection
To make an informed decision about application software or services requires an understanding of the overall marketplace. In some cases, you may not need assistance in choosing a system tool or service. In other cases, however, there can be a great deal of overlap between products and services with significant implications beyond price. ITS and the IT Governance groups can assist in reviewing and investigating competitive options and identifying possible substitutes using tools like:
STEP 2: Contract Routing and Application Review Checklist
Before a contract is routed for final review and approval of any new application or service, ATSU requires the completion of an application overview document. The overview provides key information about what is being purchased and makes it easier for reviewers to understand the purpose, the benefits, and the risks of the new investment. It includes information related to:
-
- Costs – Identify both one-time and ongoing costs. For larger investments, an evaluation may include Total Cost of Ownership (TCO) estimates which may involve internal support or external consulting/training costs.
- Data and Code Ownership – Identify the kind of data used, its security classification, and where the data will be stored. Identify whether ATSU or the vendor owns the data and the code that processes the data.
- Key Stakeholders – Identify the target audience(s) for using the service. Identify who will be involved in the implementation and ongoing support.
- Identify the Administrator(s)/Owner(s)of the service and the data
- Will this be a Pilot Implementation?
- What are the plans/possibilities for future expansion?
- Data Classification (Identifying the Authoritative data)
- Privacy Implications
- Compliance Regulations
Security Issues
-
-
- HECVAT (Higher Education Cloud Vendor Analysis Tool) – This document is used to assess the information security processes and practices of cloud application vendors. The tool assists ATSU in managing the risks to the confidentiality, integrity, and availability of sensitive institutional information and the PII of constituents. Either the full or lite version of this tool may be used, depending upon the type of system being considered.
- Backup & Disaster Recovery (Risk Assessments)
- Access Method(s) – Identify how users (and administrators) will authenticate to and access the application or service.
- SSO (Single-Sign-On)
- Portal Access
- Integrations – New applications/services should be reviewed to identify possible data integrations with other ATSU systems. Integrations should be noted in the Application Overview Summary.
- Downtime Monitoring – Identify how downtime can be monitored and how critical system/service operation is to the ongoing activities of the institution.
- Is there a process for making a Service Level Agreement (SLA) breach claim?
-
Onboarding/Training Requirements
-
-
- What type(s) of User Documentation is available?
- Is there a User Community that should be monitored and utilized?
-
Implications to Web Presence – New applications/services need to be evaluated for various impacts on the overall ATSU web portfolio.
-
-
- SEO (Search Engine Optimization)
- Branding
- Domain Names
- Accessibility (ADA) Compliance
-
Usage and Other Success Metrics
– How will implementation quality and system usage be evaluated for success?
- Are Activity Audit Trails necessary and available to key administrators?
Future Improvements
-
- Update Processes
- Options for Mobile
- Roadmap for AI
